Hey everyone! Partners, sales leaders, and friends curious about Advantech’s technology, hello!
In this era where the digital wave is sweeping everything, device security is of utmost importance. Imagine if even the very initial boot process of a device is controlled by malicious programs – wouldn’t the subsequent system security defenses be rendered useless? This is why “Secure Boot” technology is so crucial.
Recently, the cybersecurity community has focused on a security vulnerability known as CVE-2023-24932, which is related to a UEFI bootkit called BlackLotus. This malicious program can load before the operating system starts, thereby taking control of the entire system. To address this issue, Microsoft has released relevant updates and mitigation measures, including revoking old boot manager certificates.
As a leader deeply rooted in the industrial computer field, Advantech has always prioritized product security. Our engineering team has also conducted in-depth research and practical testing on this important cybersecurity update, ensuring that our products are synchronized with the latest security technologies and provide customers with the most reliable solutions.
Today, we will share with you in an easy-to-understand way about Secure Boot, this latest cybersecurity threat, and the key findings and answers discovered by the Advantech engineering team during practical testing!
What is Secure Boot? Why is it so important? #
Simply put, Secure Boot is a feature of UEFI (Unified Extensible Firmware Interface) firmware. It acts as the first gatekeeper when a device boots up, only allowing digitally signed, trusted software (such as the operating system’s boot manager) to load. This effectively prevents malicious programs (the bootkits we mentioned earlier) from stealthily infiltrating and controlling your device before the operating system starts.
Microsoft strongly recommends enabling Secure Boot to establish a secure chain of trust from the firmware to the Windows kernel. If Secure Boot is disabled, devices are highly susceptible to bootkit malware attacks. The emergence of the CVE-2023-24932 vulnerability is precisely because malicious programs found a way to bypass the Secure Boot check, so Microsoft needs to revoke some old, potentially exploitable boot manager certificates to patch this vulnerability.
Advantech Engineer Practical Testing Time: Common Questions and Answers Regarding CVE-2023-24932 #
To ensure that Advantech’s products can smoothly adopt these important cybersecurity updates and to help our customers and partners understand the potential impact, our engineering team referenced the enterprise deployment guidance published by Microsoft and conducted practical tests. Below are some of the most frequently asked and concerned questions we have compiled, along with our practical test answers:
(The following content contains more technical details, but we have tried to simplify the explanation and retain the key information from the engineer’s practical testing)
Q1. How to verify if Microsoft’s provided mitigation measures 1 (installing updated certificate definitions into DB) and 2 (updating the boot manager on the device) have been successfully applied?
A1. After deploying these two mitigation measures on the device, you can monitor for success by checking specific registry keys in the system.
If the following registry key exists:
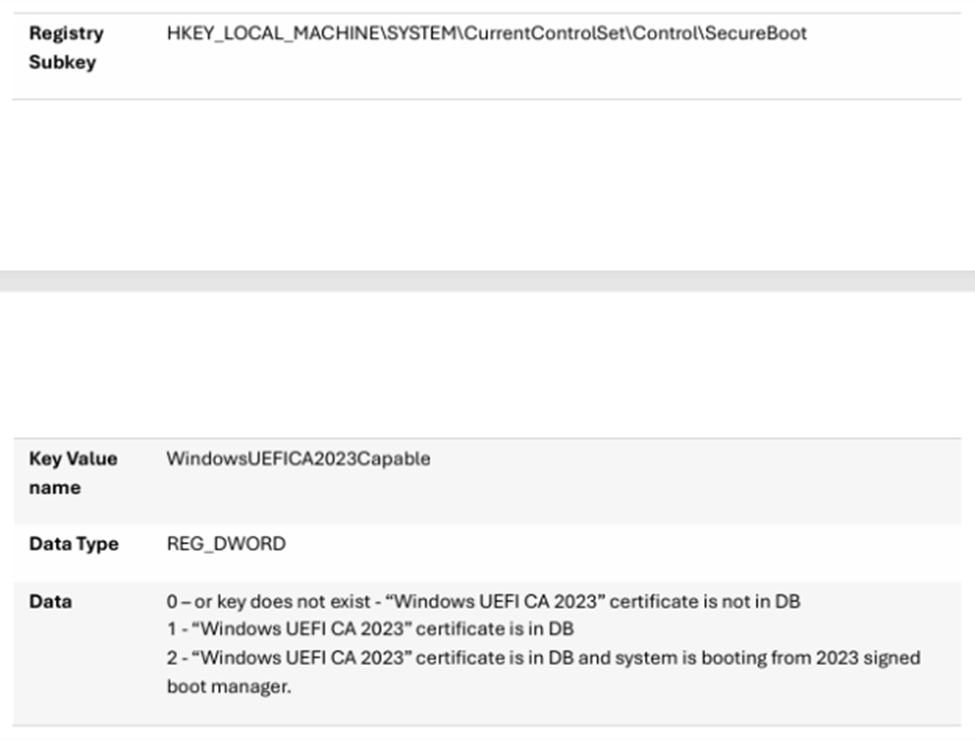
- And its value is set to
1, it indicates that the system has added the new 2023 certificate to the Secure Boot DB (Signature Database) variable. - And its value is set to
2, it indicates that the system has not only added the new 2023 certificate to the DB but is also booting using a boot manager signed by the new 2023 certificate.
Q2. If the device firmware does not have the Microsoft Corporation KEK CA 2023 and Windows UEFI CA 2023 certificates, does the user need to manually perform mitigation measures 1 and 2 to update these certificates before installing the operating system?
A2. The purpose of Mitigation 1 is to add the new Windows UEFI CA 2023 certificate to the UEFI Secure Boot Signature Database (DB). By adding this certificate to the DB, the device firmware will trust Microsoft Windows boot applications signed by this new certificate. Mitigation 2 then applies the new version of the Windows Boot Manager signed by the new Windows UEFI CA 2023 certificate.
These mitigations are very important for the long-term Windows serviceability of these devices. Because the Microsoft Windows Production PCA 2011 certificate in the firmware will expire in October 2026, devices must have the new Windows UEFI CA 2023 certificate added to the firmware before this date, otherwise the device will no longer be able to receive Windows updates and will thus be in an insecure state.
More information can be found here: Enterprise Deployment Guidance for CVE-2023-24932 - Microsoft Support
Q3. After installing the operating system, is it necessary to manually move the Windows Production PCA 2011 certificate to the Secure UEFI Disabled List (DBX)?
A3. Technically yes, but OEMs should exercise caution when performing this step and fully understand the potential impact on customers. It is best to leave this step/decision to the end customer’s discretion.
Q4. Does Microsoft have future plans to completely remove PCA 2011 from the database? If so, is there a timeline?
A4. PCA 2011 will expire later next year (2026). As such, we anticipate that future OEM systems will choose not to include it in firmware. We also anticipate continuing to provide guidance for existing/older systems on adding this PCA to the DBX as a means of ensuring full protection against rollback attacks (such as Blacklotus).
Q5. Are there plans to update the EFI image certificate in WS2022 to PCA 2023? If so, will this change also be reflected in the WS2022 ISO file, similar to WS2025?
A5. All older versions of the Windows operating system can be converted to use the boot manager signed by the 2023 PCA. There are currently no plans to update the default settings of any older operating system boot media that Microsoft may release, but this may be reconsidered in the future.
Q6. I have applied the certificate revocations on my device and now need to reinstall or restore the device. Why can’t I boot the device using my recovery media (CD/DVD, PXE Boot, USB drive)?
A6. Please refer to the Recovery Procedure section in the Microsoft article to restore the device.
And follow the guidance in the Troubleshooting Boot Issues section.
Q7. My device uses multiple operating systems. How should I update my system?
A7. Before applying the certificate revocations, update all Windows operating systems using updates released on or after July 9, 2024. After applying the certificate revocations, any version of Windows not updated to at least the July 9, 2024 update may fail to boot. Please follow the guidance in the Troubleshooting Boot Issues section.
Q8. Which boot error messages might be related to the security enhancements described in this article?
A8. Please refer to the Troubleshooting Boot Issues section.
Q9. What is the impact of these mitigations on existing Windows installation media?
A9. Applying mitigations 3 (enabling revocations) and 4 (applying SVN updates to firmware) will prevent older, vulnerable boot managers from running. This will cause existing Windows installation media to fail to boot until that media has been updated with the new boot manager. This includes ISO images, bootable USB drives, and network boot (PxE and HTTP boot). Therefore, it is essential to thoroughly test these changes in your environment before proceeding.
Q10. When creating OS media using the Make2023BootableMedia.ps1 script, does it only update the boot manager signed by the Windows UEFI CA 2023 certificate? Does the script provide any mechanism or instructions to update the necessary Secure Boot certificates missing in the device firmware?
A10. Yes, the script will only update the media to use the boot manager signed by the “Windows UEFI CA 2023”. The script does not provide any mechanism to update the system’s Secure Boot certificates. This script can be used to create media for any system, so no assumptions can be made about the underlying system it may be run on.
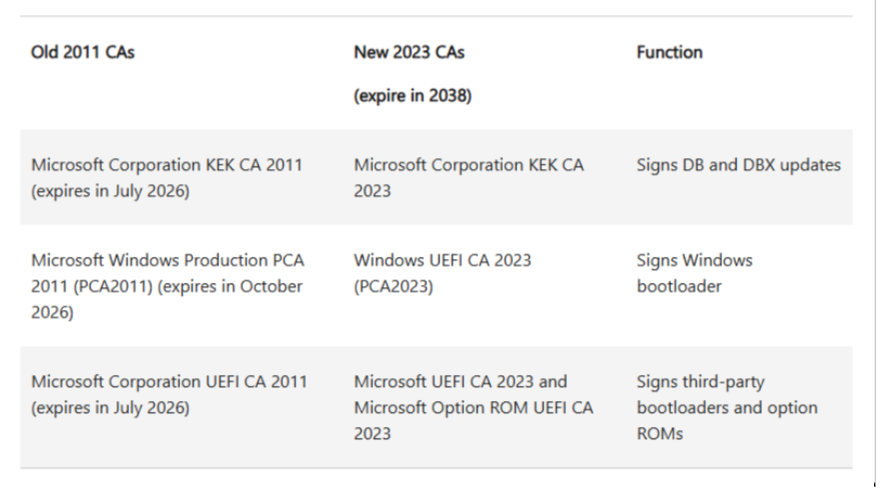
Q11. Can you provide details on when the older 2011 CA and the newer 2023 CA expire and the features they support?
A11. Please refer to the table below for details on the 2011 and 2023 CAs, including their expiration dates and associated features. This information can also be found here: Enterprise Deployment Guidance for CVE-2023-24932 - Microsoft Support
Advantech’s Value and Continuous Innovation #
From this practical testing and Q&A, we can clearly see that even the underlying boot security requires continuous attention and updates. Especially the certificate expiration issue reminds us that we must plan ahead to ensure the long-term security and stable operation of devices.
This practical testing by the Advantech engineering team is a testament to our proactive response to the latest cybersecurity challenges. We not only focus on operating system-level security but also delve into firmware and the boot process to ensure that every device provided by Advantech has a solid security foundation. By testing and verifying these important Microsoft updates in advance, we can:
- Ensure Advantech product compatibility: Before Microsoft fully promotes these updates, we have conducted internal testing to ensure that our hardware platforms can work smoothly with the new boot managers and certificates.
- Provide customers with reliable deployment recommendations: Our practical testing experience can be translated into specific deployment guides and technical support to help customers smoothly adopt updates and avoid potential boot issues.
- Demonstrate Advantech’s R&D strength: This work proves Advantech’s continuous investment and professional capabilities in underlying technology and cybersecurity. We are capable of addressing complex technical challenges and providing customers with leading solutions.
Conclusion and Future Outlook #
Secure Boot and related certificate management are key components in ensuring device security from the very beginning of the boot process. The CVE-2023-24932 vulnerability and the subsequent certificate updates once again remind us that cybersecurity protection requires comprehensive and continuous efforts.
Advantech will continue to closely monitor the latest information released by Microsoft and other cybersecurity organizations and integrate relevant security updates and technologies into our product development and support processes. We encourage all customers and partners using Advantech products to pay close attention to these important cybersecurity updates and conduct thorough testing before deployment.
If you encounter any issues during the process of adopting these updates or require more in-depth technical support, please feel free to contact your Advantech sales representative or technical support team. We are always ready to provide assistance!
In the future, Advantech will also continue to invest in the research and development of cutting-edge technologies such as firmware security and hardware root of trust, providing more secure and reliable industrial IoT solutions for various industries. Please continue to follow Advantech’s technical blog for more exciting technical sharing!